Today I discovered…
PentestGPT
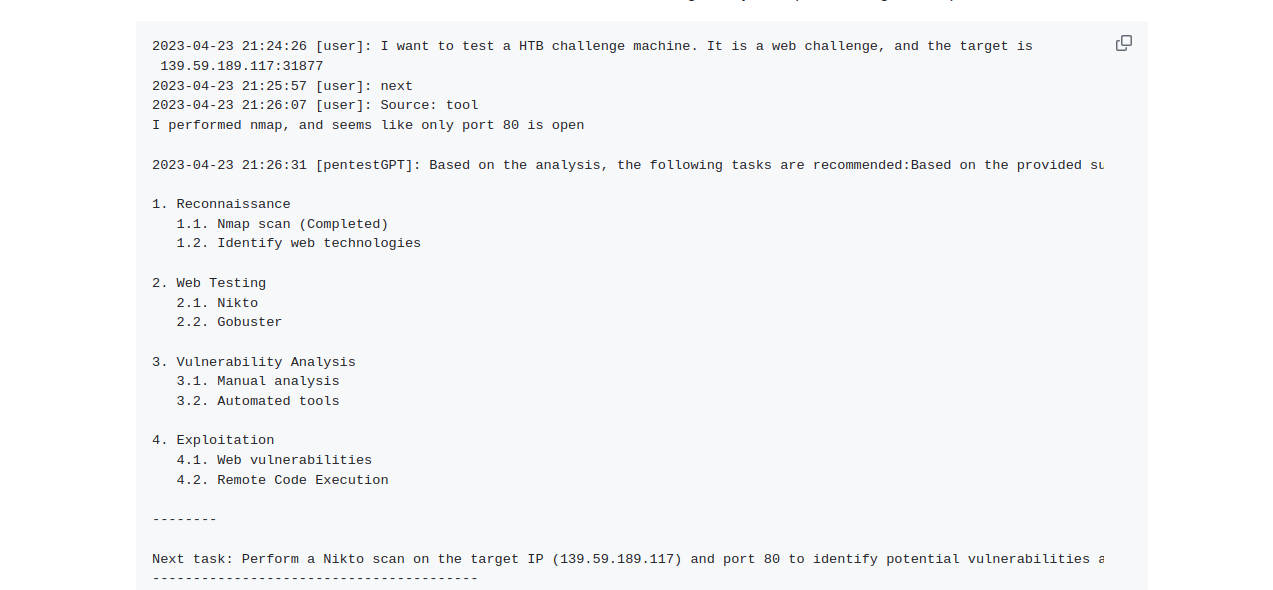
A CLI to assist with penetration testing. The program starts with some pre-defined prompts and then creates a ToDo list for pen testing your website/systems and making them more secure. It suggests the next action item and the command to execute and move forward from there step by step via an interactive mode.
💖 What I like:
Great tool to learn pen testing: It is a great tool to learn penetration testing by doing things. It prepares the plan and picks the next action item for you to execute. You can discuss the plan and steps in details with it to dive deeper into the topic at hand.
Safer than AutoGPT: While AutoGPT operates on the same principles of planning and reasoning, PentestGPT only runs in interactive mode. It does not execute commands on its own, reducing the risk of performing malicious operations to a minimum.
👎 What I dislike:
Bugs: It had some blocker issues such as the CLI did not work on critical step when the user needs to choose the source of information.
Token limit: As it goes with all other GPT based projects, the token limit makes it unusable in most cases. Although, it does have summarization feature built-in but I didn’t see it doing the job properly for my use case. But that won’t be a big concern once some bugs are fixed and the latest 16k context GPT model is supported. Looking at where this project is today, I’m estimating the resolution is just 1-2 releases away only.
Requires inputs/knowledge from the tester: I had higher expectations for this project. I anticipated that there would be no need to copy and paste command results and that the tool would be more automated. However, my perspective on the tool shifted after using it. Instead of considering it as an automation tool, I began to see it as a learning tool.
Author: Gelei Deng
Demo | Source
Tech Stack: Python, OpenAI GPT API, LangchainIf you discovered an interesting Open-Source project and want me to feature it in the newsletter, get in touch via the form above. To support this newsletter and Open-Source authors, follow #OpenSourceDiscovery on LinkedIn and Twitter